These are my writeups for osu!gaming CTF 2024.
blockchain/scorechain
Snipe mr nathan on osu and claim the bounty in the very secure blockchain bancho!
nc chal2.osugaming.lol 8000
— Triacontakai
This problem was my first time working with blockchain problems. I was provided the file dist.zip, where it was a Rust Solana blockchain problem.
Initially looking at the dist.zip, this is the directory of the challenge
| |
After reading the README.md, we are aware that we should
| |
First, we take a look at the framework folder.
If we take a look at framework/src/main.rs, we can see
| |
In the above, we can see two things that happen
- an initial setup where player “cookiezi” is given a large sum of money.
- the server then processes a “SubmitPlay” instruction, which allows for the submission of a play that meets specific bounty amount
from looking at the above code,we are aware that we can exploit the SubmitPlay, as it doesn’t properly validate the required conditions where bounty payout should happen, and doesn’t make sure that the play submitted meets specific criteria beyond the control of the submitting player
We can write our solution code inside the provided initialize function in the framework-solve/solve/programs/solve/src/lib.rs file that is specifically for writing the solution code, where we have:
| |
Looking closely, this is the specific code we wrote
| |
And this works, as we can verify this locally
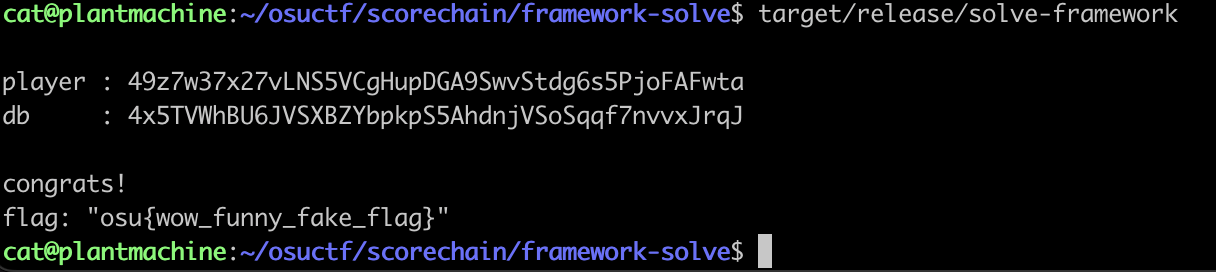
And after changing in framework-solve/src/main.rs to nc to the challenge server
| |
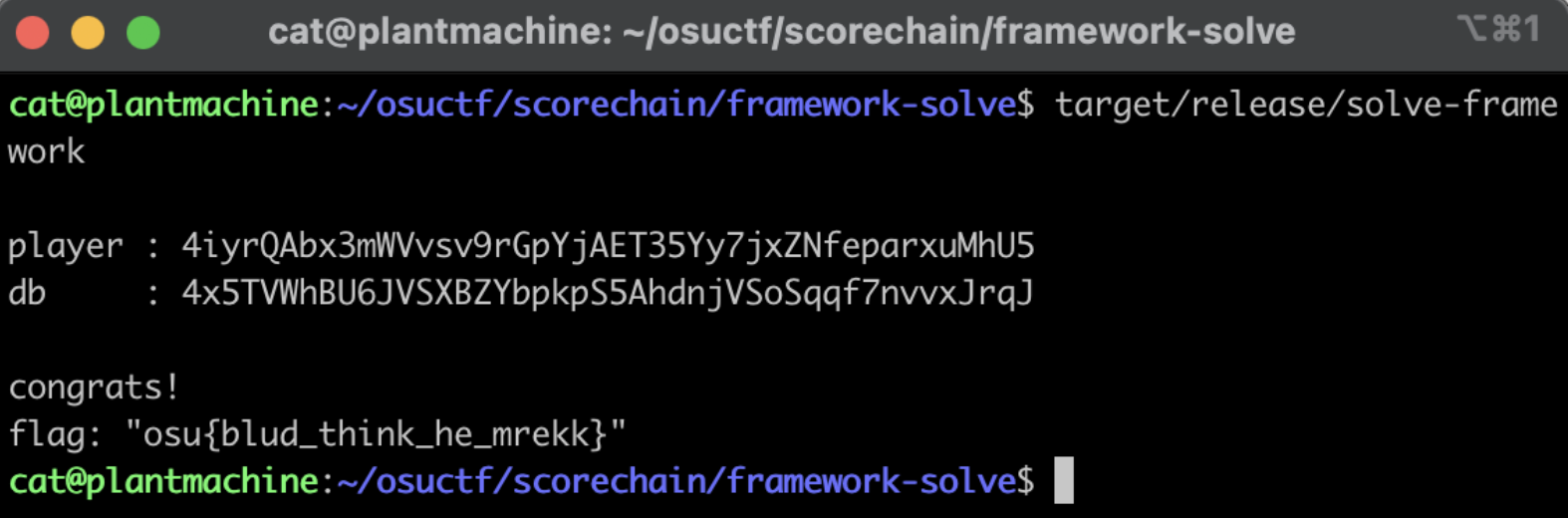
We are able to run the solve script again and we get the flag osu{blud_think_he_mrekk}.
reverse/SAT-before-osu
My mom won’t let me play osu if I don’t study for the SAT but this looks nothing like it! Please help me! T^T
— BrokenAppendix
In this challenge, we’re given the below system of equations that I’ve put into constraints. This is a set of systems and equations that can be easily solved with the z3 theorem prover.
| |
The flag that we get is osu{0rZ_p3PpY_my_s4v1oR}
crypto/base727
We’re given the file 727.py along with the encoded flag 06c3abc49dc4b443ca9d65c8b0c386c4b0c99fc798c2bdc5bccb94c68c37c296ca9ac29ac790c4af7bc585c59d.
To decrypt, we write a script that is able to decode from a base727 encoded string to text, and decrypt the encoded flag:
| |
And we get the flag osu{wysiwysiwysiywsywiwywsi}
